

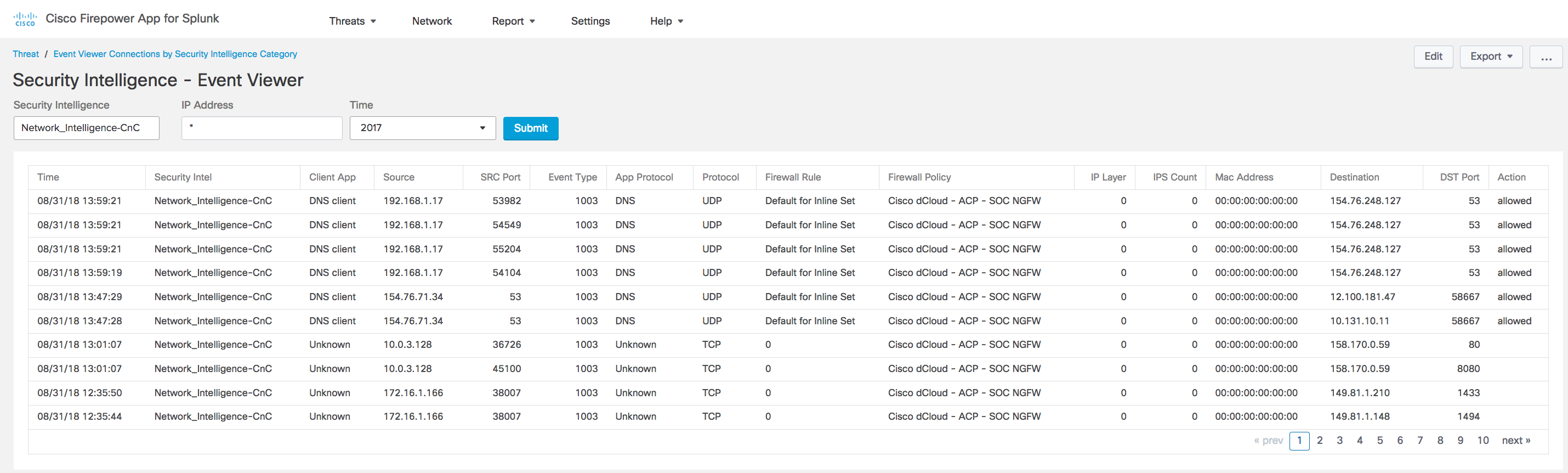
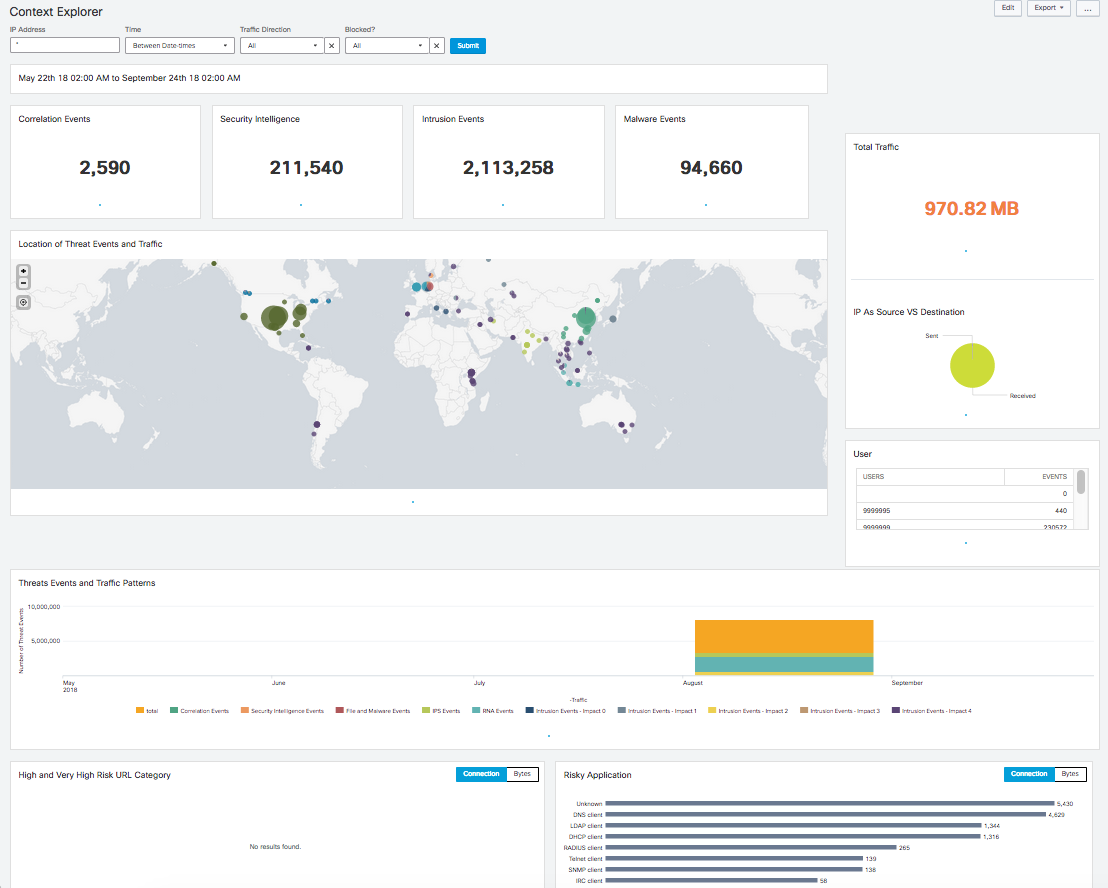
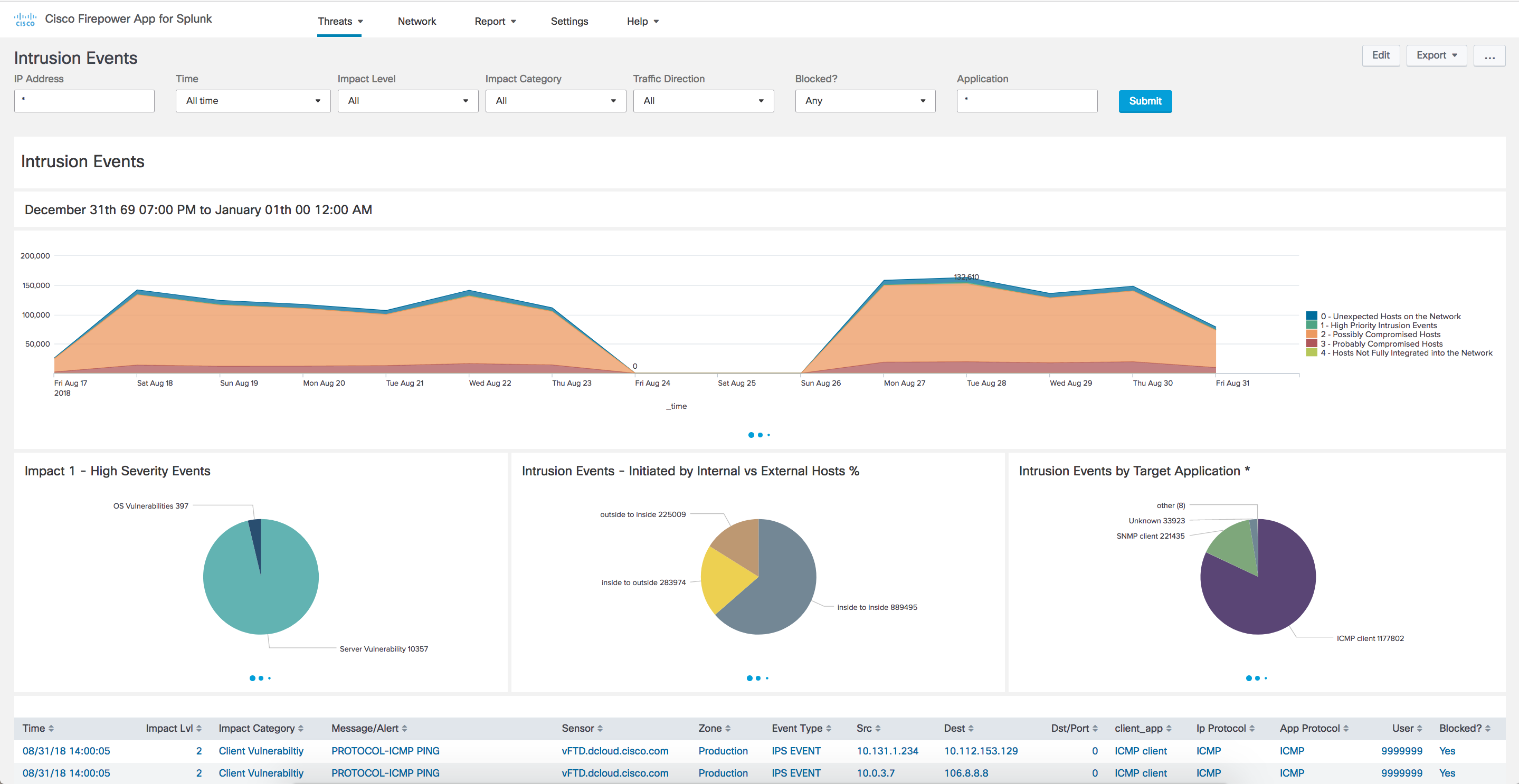










A User Guide is published here https://cisco.com/go/firepower-for-splunk
TELL US WHAT WILL MAKE THIS APP BETTER FOR YOU! We want your feedback and any feature requests. Please email fp-4-splunk@cisco.com with any requests.
Version 1.9.0
Fixed bugs in Networking and Reporting searches
Modified search queries to ignore non-existent fields in aggregate queries
Modified Threat Summary to include Malware Threat Score Summary panel and Security Intel Event Timeline
Fixed issues in Context Explorer
v1.8.1
*Removed unnecessary .conf files for cloud compliance and validation
v1.8.0
Removed REST calls to determine FMC configuration information used in queries to determine traffic direction
Added filters for ingress/egress traffic to replace Traffic Direction field
*Updated Analytic Displays for IDS and Threat Analysis dashboards
*Removed references to older non-compliant jQuery libraries
*Updated app to comply with the latest cloud requirements
Build in dual-compatibility for both ftd syslog and estreamer data, analytics will dynamically adjust to either source type
Build in support for CVE lookup via Snort Rule Id (SID)
Updated transforms.conf and props.conf to normalize field naming conventions between both ftd syslog and estreamer data sets
VPN Events dashboard was added to provide enhanced visibility on Firepower Device data
Added "Device Overview" Panel which shows VPN Login/Logoff Events
Fixed bug with security intel list on the "Threats" page
Modified app to conform to cloud certification requirements
Modified app to conform to cloud certification requirements
Removed setup.xml, users can directly modify the homenet.csv to determine inbound/outbound traffic
Firepower App for Splunk v 1.3.7
Release to Splunkbase 10/21/2019
v1.3.7 Updates -
Cleaned up UI on Threats Summary page, and Context Explorer
Modified queries to reflect encore changes, specifically querying filtered "Blocked" now uses the blocked field vs the action field.
Modified Data In/Out metrics on Context Explorer
Modified Umbrella Experience
Cisco Firepower App for Splunk presents security and network event information sent to Splunk from Firepower Management Center running version 6.0 or later.
To bring your Firepower data into Splunk, you must use the Cisco eStreamer eNcore Add-on for Splunk. This technical add-on (TA) is available from https://splunkbase.splunk.com/app/3662/.
The types of data available for analysis are described at https://splunkbase.splunk.com/app/3662/.
Features include:
Presents critical Firepower event information
Threat Summary Dashboard
Intrusion Events with Enrichment for Threat Hunting
Network Summary Dashboard
Context Explorer
Table Views
Event Filters
Firepower App for Splunk v 1.3.5
Release to Splunkbase 9/23/2019
v1.3.5 Updates -
*removed issues that prevented version 1.3.2 from being cloud certified
Cisco Firepower App for Splunk presents security and network event information sent to Splunk from Firepower Management Center running version 6.0 or later.
To bring your Firepower data into Splunk, you must use the Cisco eStreamer eNcore Add-on for Splunk. This technical add-on (TA) is available from https://splunkbase.splunk.com/app/3662/.
The types of data available for analysis are described at https://splunkbase.splunk.com/app/3662/.
Features include:
Presents critical Firepower event information
Threat Summary Dashboard
Intrusion Events with Enrichment for Threat Hunting
Network Summary Dashboard
Context Explorer
Table Views
Event Filters
Firepower App for Splunk v 1.3.2
Release to Splunkbase 7/5/2019
v1.3.2 Updates -
Fixed duplicate dashboard metric on front page for security intel events
Added more reports to the "Reports" tab
Cisco Firepower App for Splunk presents security and network event information sent to Splunk from Firepower Management Center running version 6.0 or later.
To bring your Firepower data into Splunk, you must use the Cisco eStreamer eNcore Add-on for Splunk. This technical add-on (TA) is available from https://splunkbase.splunk.com/app/3662/.
The types of data available for analysis are described at https://splunkbase.splunk.com/app/3662/.
Features include:
Presents critical Firepower event information
Threat Summary Dashboard
Intrusion Events with Enrichment for Threat Hunting
Network Summary Dashboard
Context Explorer
Table Views
Event Filters
Firepower App for Splunk v 1.3.1
Release to Splunkbase 5/22/2019
v1.3.1 Updates -
*Updated content to conform to Splunk Cloud Certification standards
Cisco Firepower App for Splunk presents security and network event information sent to Splunk from Firepower Management Center running version 6.0 or later.
To bring your Firepower data into Splunk, you must use the Cisco eStreamer eNcore Add-on for Splunk. This technical add-on (TA) is available from https://splunkbase.splunk.com/app/3662/.
The types of data available for analysis are described at https://splunkbase.splunk.com/app/3662/.
Features include:
Presents critical Firepower event information
Threat Summary Dashboard
Intrusion Events with Enrichment for Threat Hunting
Network Summary Dashboard
Context Explorer
Table Views
Event Filters
Firepower App for Splunk v 1.2.9
Release to Splunkbase 4/24/2019
v1.2.9 Updates -
*Removed default enabled=true for the pythons scripts that support Umbrella, as well as removed other unused python scripts
Cisco Firepower App for Splunk presents security and network event information sent to Splunk from Firepower Management Center running version 6.0 or later.
To bring your Firepower data into Splunk, you must use the Cisco eStreamer eNcore Add-on for Splunk. This technical add-on (TA) is available from https://splunkbase.splunk.com/app/3662/.
The types of data available for analysis are described at https://splunkbase.splunk.com/app/3662/.
Features include:
Presents critical Firepower event information
Threat Summary Dashboard
Intrusion Events with Enrichment for Threat Hunting
Network Summary Dashboard
Context Explorer
Table Views
Event Filters
Firepower App for Splunk v 1.2.7
Release to Splunkbase 4/19/2019
v1.2.7 Updates -
Umbrella Investigate is now here! Using the Event viewer you can now pull in Umbrella threat feeds. Requires Umbrella API Token
Modifications made to adhere to Splunk Cloud certification requirements
*Settings has moved to traditional app/settings page
Cisco Firepower App for Splunk presents security and network event information sent to Splunk from Firepower Management Center running version 6.0 or later.
To bring your Firepower data into Splunk, you must use the Cisco eStreamer eNcore Add-on for Splunk. This technical add-on (TA) is available from https://splunkbase.splunk.com/app/3662/.
The types of data available for analysis are described at https://splunkbase.splunk.com/app/3662/.
Features include:
Presents critical Firepower event information
Threat Summary Dashboard
Intrusion Events with Enrichment for Threat Hunting
Network Summary Dashboard
Context Explorer
Table Views
Event Filters
Firepower App for Splunk v 1.1.3
Release to Splunkbase 2/27/2019
v1.1.3 Updates -
Modified Event Viewer to Link back to the FMC for IPs (Network Mapping) and Malware Hashes (File Trajectory)
Modified Event Viewer to adhere to Cisco branding schemes
*Fixed issue with Action/Blocked Filters not being used in search queries
Cisco Firepower App for Splunk presents security and network event information sent to Splunk from Firepower Management Center running version 6.0 or later.
To bring your Firepower data into Splunk, you must use the Cisco eStreamer eNcore Add-on for Splunk. This technical add-on (TA) is available from https://splunkbase.splunk.com/app/3662/.
The types of data available for analysis are described at https://splunkbase.splunk.com/app/3662/.
Features include:
Presents critical Firepower event information
Threat Summary Dashboard
Intrusion Events with Enrichment for Threat Hunting
Network Summary Dashboard
Context Explorer
Table Views
Event Filters
Firepower App for Splunk v 1.1.2
Release to Splunkbase 2/19/2019
v1.1.2 Updates -
Modified queries to utilize configurable index located in Marco settings
Added Event Viewer for Correlation Events
Cisco Firepower App for Splunk presents security and network event information sent to Splunk from Firepower Management Center running version 6.0 or later.
To bring your Firepower data into Splunk, you must use the Cisco eStreamer eNcore Add-on for Splunk. This technical add-on (TA) is available from https://splunkbase.splunk.com/app/3662/.
The types of data available for analysis are described at https://splunkbase.splunk.com/app/3662/.
Features include:
Presents critical Firepower event information
Threat Summary Dashboard
Intrusion Events with Enrichment for Threat Hunting
Network Summary Dashboard
Context Explorer
Table Views
Event Filters
Cisco Firepower App for Splunk
v1.1.1 updates
Fixed issue with cross link to FMC on Threats->Dashboard->Indications of Compromise dashboard, previously the FMC ip didn't not load into the right click menu option
Release notes
Firepower App for Splunk v1.1
Updates for v1.1 include fully validated by Splunk App Inspect
Modification to Intrusion Events Dashboard, displaying High Priority Events by Class Description
*Cross Links back to FMC for File Trajectory on Host IoC Dashboard
Cisco Firepower App for Splunk presents security and network event information sent to Splunk from Firepower Management Center running version 6.0 or later.
To bring your Firepower data into Splunk, you must use the Cisco eStreamer eNcore Add-on for Splunk. This technical add-on (TA) is available from https://splunkbase.splunk.com/app/3662/.
The types of data available for analysis are described at https://splunkbase.splunk.com/app/3662/.
Features include:
Presents critical Firepower event information
Threat Summary Dashboard
Intrusion Events with Enrichment for Threat Hunting
Network Summary Dashboard
Context Explorer
Table Views
Event Filters
Link Backs for File Trajectory, Host Profiles, Packet View
As a Splunkbase app developer, you will have access to all Splunk development resources and receive a 10GB license to build an app that will help solve use cases for customers all over the world. Splunkbase has 1000+ apps from Splunk, our partners and our community. Find an app for most any data source and user need, or simply create your own with help from our developer portal.