











The Cybereason for Splunk App is fully supported by Cybereason. For any queries please visit https://nest.cybereason.com/
z
| Author | Metron Labs, Cybereason |
| App Version | 2.0.2 |
| App Build | 184 |
| Vendor Products | Cybereason |
| Has index-time operations | true, the included TA add-on must be placed on the indexers |
| Creates an index | false |
| Implements summarization | Currently, the app does not generate summaries |
About Cybereason For Splunk
Version 2.0.2 of Cybereason For Splunk is compatible with:
| Splunk Enterprise versions | 8.2 or higher |
| Platforms | Splunk Enterprise, Splunk Cloud |
Compatability
The Cybereason App for Splunk enables you to gain deep insight & visibility into your endpoints, detect advanced attacks based on AI hunting, and take response actions within Splunk. The Cybereason AI Hunting Engine automatically asks a complex set of questions of data collected from all of your endpoints at a rate of 8 million calculations per second, 24 hours a day, 7 days a week. This means the solution is continuously hunting on your behalf by asking the same sorts of questions advanced security analysts would ask as they hunt for threats inside an environment. The difference, however, is that the Cybereason malicious activity models run constantly, and continually adapt and evolve according to the data the solution receives and analyzes.
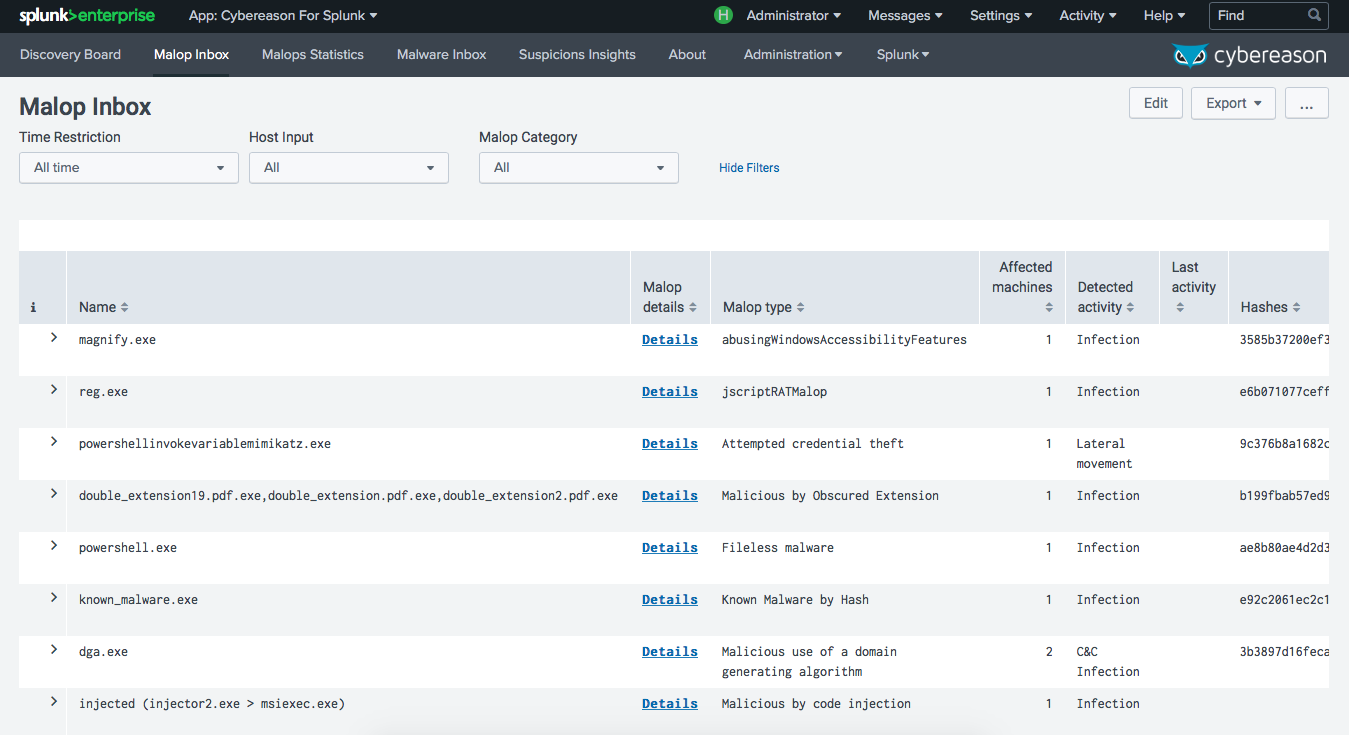
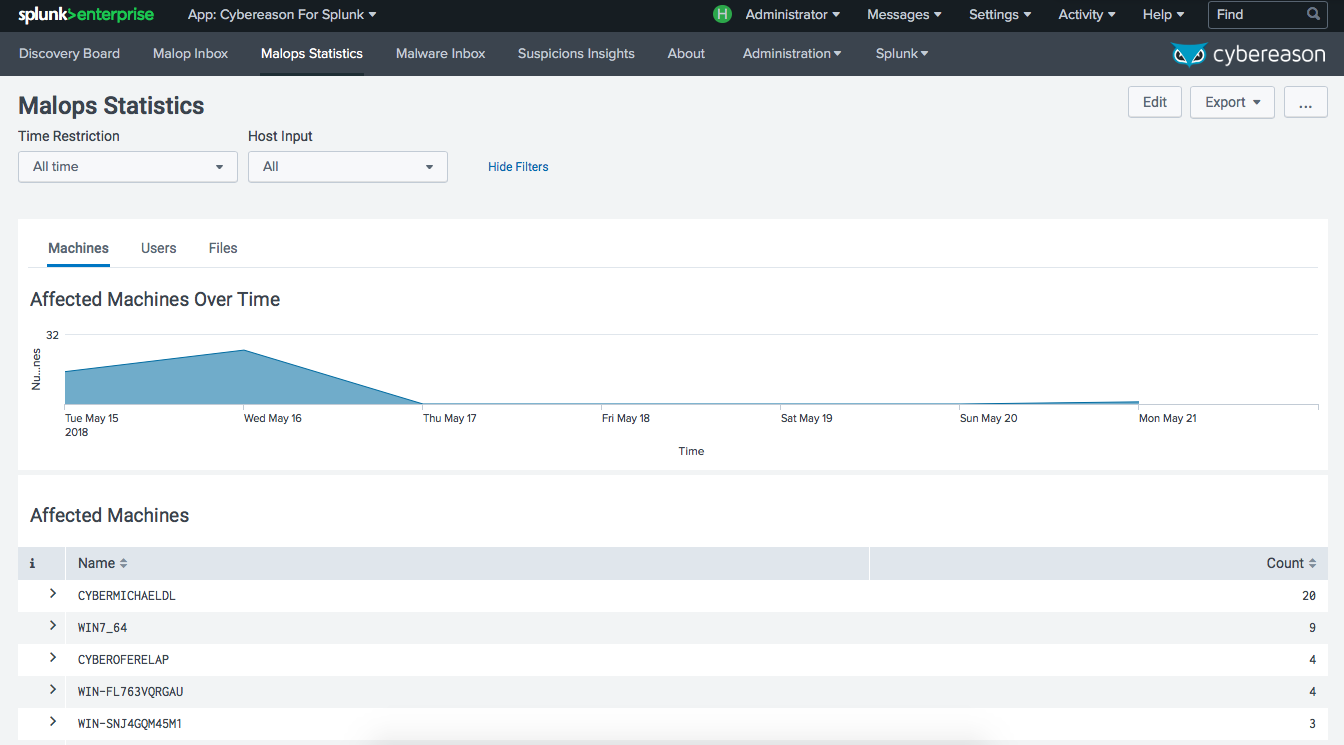
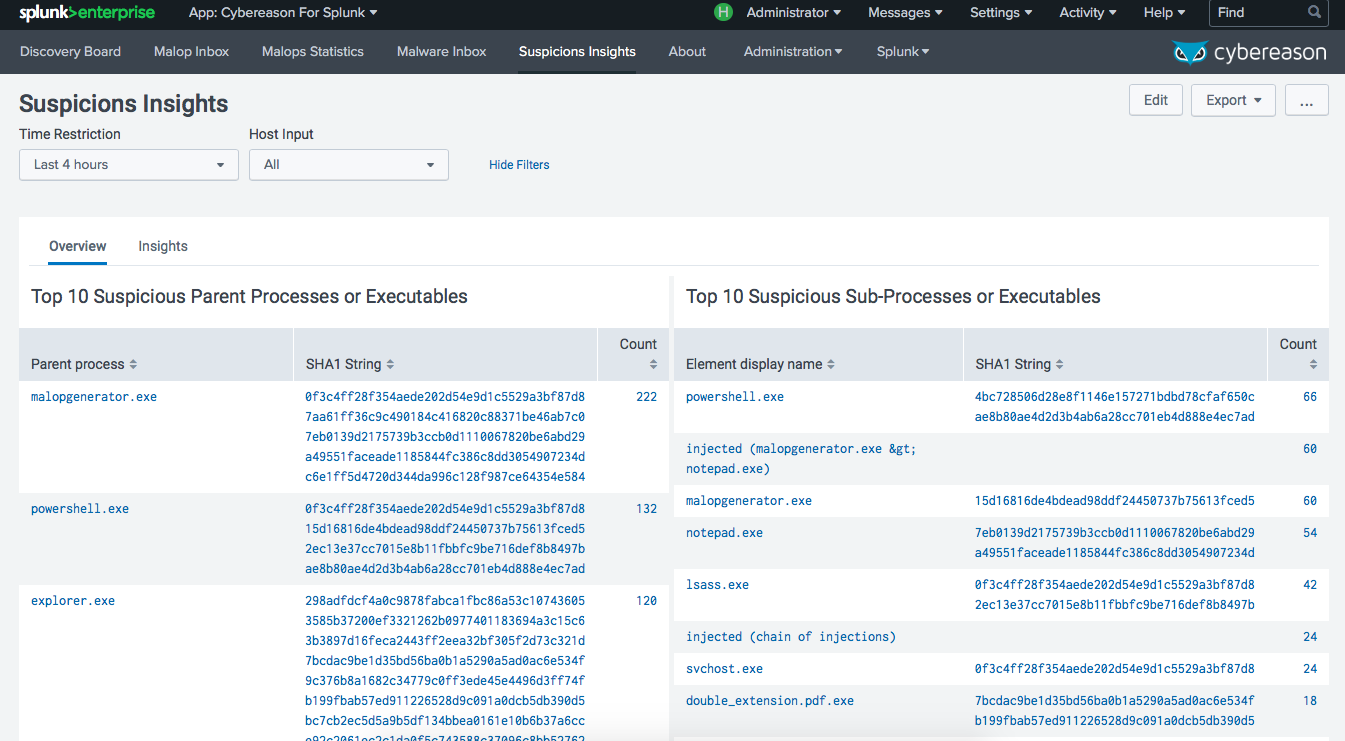
When the Cybereason AI Hunting Engine identifies malicious behavior, its classified based on context and severity. Suspicions represent multiple pieces of anomalous behavior which are related and therefore more likely to be malicious. Malops (malicious operations) are a collection of related suspicious activities that are highly likely to indicate a security incident, and are defined in a way that minimizes the likelihood of analysts spending time investigating benign activities or false positives. Both Suspicions and Malops are presented in Splunk along with insights that give context to the alerts so you can quickly understand what is happening in your environment.
This App provides the following scripts:
| cybereason.py | This python file controls the ability to interface with Cybereason. |
| cybereason_rest_client.py | This Python class allows re-use of the cybereason api for various applications. |
| Diag.py | Allows diag-targeted collection of information. |
| ModularInput.py | Inheritable Class to create Modular Inputs |
| Utilities.py | Allows utility interactions with Splunk Endpoints |
Access questions and answers specific to Cybereason For Splunk at https://answers.splunk.com . Be sure to tag your question with the App.
Support Email: support@cybereason.com
Support Offered: Email, Community Engagement
Support is available via email at support@cybereason.com.
Because this App runs on Splunk Enterprise, all of the Splunk Enterprise system requirements apply.
Download Cybereason For Splunk at https://splunkbase.splunk.com.
NOTE: Where referenced, the Cybereason Addon For Splunk is located on Splunkbase.
Follow these steps to install the app in a single server instance of Splunk Enterprise:
Have your Splunk Cloud Support handle this installation. Do NOT install the Addon on the same system as the App.
You may consider using an on-premise Heavy Forwarder to install Cybereason Addon For Splunk, and send the logs to Splunk Cloud.
For each Search Head in the environment, deploy a non-configured copy of the App. DO NOT SEND Cybereason Addon For Splunk to a Search Head Cluster (SHC).
For a single Data Collection Node OR Heavy Forwarder (a full instance of Splunk is required), install Cybereason Addon For Splunk and configure through the GUI.
By default all events will be written to the main index. You should change the index in the configuration files to match your specific index.
Check the Monitoring Console (>=v6.5) for errors
Visit the Application Health dashboard
Check for errors using following queries:
index=_internal sourcetype=modularinput OR sourcetype=restclient log_level=ERRORindex=<yourindex> sourcetype=CybereasonForSplunk:errorExecute $SPLUNK_HOME/bin/splunk diag --collect app:CybereasonForSplunk and send the diag to Cybereason Support.
Cybereason For Splunk contains the following lookup files.
labels.csv - contains the labels for use with the Cybereason data
malop_types.csv - a lookup that helps drive panels
Version 2.0.2 of Cybereason For Splunk incorporates the following Third-party software or third-party services.
This program is free software; you can redistribute it and/or modify it under the terms of the GNU General Public License as published by the Free Software Foundation; either version 2 of the License, or (at your option) any later version.
This program is distributed in the hope that it will be useful, but WITHOUT ANY WARRANTY; without even the implied warranty of MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU General Public License for more details.
You should have received a copy of the GNU General Public License along with this program; if not, write to the Free Software Foundation, Inc., 51 Franklin Street, Fifth Floor, Boston, eMA 02110-1301, USA.
PYTHON SOFTWARE FOUNDATION LICENSE VERSION 2
1. This LICENSE AGREEMENT is between the Python Software Foundation (PSF), and the Individual or Organization (Licensee) accessing and otherwise using this software (Python) in source or binary form and its associated documentation.
2. Subject to the terms and conditions of this License Agreement, PSF hereby grants Licensee a nonexclusive, royalty-free, world-wide license to reproduce, analyze, test, perform and/or display publicly, prepare derivative works, distribute, and otherwise use Python alone or in any derivative version, provided, however, that PSFs License Agreement and PSFs notice of copyright, i.e., Copyright (c) 2001, 2002, 2003, 2004, 2005, 2006, 2007, 2008 Python Software Foundation; All Rights Reserved are retained in Python alone or in any derivative version prepared by Licensee.
3. In the event Licensee prepares a derivative work that is based on or incorporates Python or any part thereof, and wants to make the derivative work available to others as provided herein, then Licensee hereby agrees to include in any such work a brief summary of the changes made to Python.
4. PSF is making Python available to Licensee on an AS IS basis. PSF MAKES NO REPRESENTATIONS OR WARRANTIES, EXPRESS OR IMPLIED. BY WAY OF EXAMPLE, BUT NOT LIMITATION, PSF MAKES NO AND DISCLAIMS ANY REPRESENTATION OR WARRANTY OF MERCHANTABILITY OR FITNESS FOR ANY PARTICULAR PURPOSE OR THAT THE USE OF PYTHON WILL NOT INFRINGE ANY THIRD PARTY RIGHTS.
5. PSF SHALL NOT BE LIABLE TO LICENSEE OR ANY OTHER USERS OF PYTHON FOR ANY INCIDENTAL, SPECIAL, OR CONSEQUENTIAL DAMAGES OR LOSS AS A RESULT OF MODIFYING, DISTRIBUTING, OR OTHERWISE USING PYTHON, OR ANY DERIVATIVE THEREOF, EVEN IF ADVISED OF THE POSSIBILITY THEREOF.
6. This License Agreement will automatically terminate upon a material breach of its terms and conditions.
7. Nothing in this License Agreement shall be deemed to create any relationship of agency, partnership, or joint venture between PSF and Licensee. This License Agreement does not grant permission to use PSF trademarks or trade name in a trademark sense to endorse or promote products or services of Licensee, or any third party.
8. By copying, installing or otherwise using Python, Licensee agrees to be bound by the terms and conditions of this License Agreement.
Released under the MIT license.
Permission is hereby granted, free of charge, to any person obtaining a copy of this software and associated documentation files (the Software), to deal in the Software without restriction, including without limitation the rights to use, copy, modify, merge, publish, distribute, sublicense, and/or sell copies of the Software, and to permit persons to whom the Software is furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED AS IS, WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.
https://github.com/jquery/jquery/blob/master/LICENSE.txt
Copyright JS Foundation and other contributors, https://js.foundation/
This software consists of voluntary contributions made by many individuals. For exact contribution history, see the revision history available at https://github.com/jquery/jquery
The following license applies to all parts of this software except as documented below:
Permission is hereby granted, free of charge, to any person obtaining a copy of this software and associated documentation files (the Software), to deal in the Software without restriction, including without limitation the rights to use, copy, modify, merge, publish, distribute, sublicense, and/or sell copies of the Software, and to permit persons to whom the Software is furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED AS IS, WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.
All files located in the node_modules and external directories are externally maintained libraries used by this software which have their own licenses; we recommend you read them, as their terms may differ from the terms above.
https://github.com/d3/d3/blob/master/LICENSE
Copyright 2010-2016 Mike Bostock All rights reserved.
Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following conditions are met:
Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer.
Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer in the documentation and/or other materials provided with the distribution.
Neither the name of the author nor the names of contributors may be used to endorse or promote products derived from this software without specific prior written permission.
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS AS IS AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT OWNER OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
2021, Metron Labs
Dashboard updated to display data for EPP Malops as well
Minor bug fixes
Removed App Configuration.
Increased Malop Comments limit to 3000 characters.
Added 'Add User' action logs
Improvement
- Upgraded dashboards to version 1.1 so that they work with Splunk Cloud 8.2
Improvement
- Added suffix to child processes of Webshell malops for better identification
- Handled an exception while fetching server info for User agent
- Corrected the title of a panel in the Discovery board
Improvement
- Better encryption facility for JWT authentication mode
Improvement
- Comments are now included in the malop events
- New filters for User Action Logs for better querying
- Query enhancements for action logs
- Logging improvement for successful login
Documentation
- Added the steps to update credentials for an existing input
Feature
- A new feature to turn off Logon Session data input from the user configuration settings
Improvement
- Better error handling for processing events
- Defined a new macro to query action logs in order to improve flexibility
Bug
- Resolved some issues related to User action logs
- Generating a new JWT token for authorization once the previous JWT has expired
- Removed a duplicate About tab from the app configuration page
Improvement
- The api headers is updated to contain User-agent detail which will include the application version and server address
- The app now has the capability to log stacktrace if any exception occurs
- User action logs are downloaded in the log directory path and removed after they have been processed
Enhancement
- Enabled the global field extraction for the app
- Added the action field for malop and malware events so that events get tagged correctly by the malware data model
Bug
- Added a validation while fetching child processes for webshell typed malops
Bug
- Minor event type change in the User audit log filter
Improvement
- User action logs can now be configured using User Activity Input button which has a default interval of 24h as it has a significant footprint.
Enhancements
- User Activity Input button for polling users data with default interval time of 24 hours.
- All new dashboard to monitor action logs
- Severity values for Malop inbox table
- Option to authenticate using JWT token
- Removed troubleshooting logs to make the app space efficient
- Authentication data model to keep track of user log-ins once every 24h
- Webshell malop will now contain all of the child processes (and their children, and so on)
Bug
- Fixed duplicate malwares bug to make the app more memory efficient
- Resolved broken pipe error that obstructed the app's execution sometimes
- Added missing validations to improve application workflow
Updates for Splunk Cloud
As a Splunkbase app developer, you will have access to all Splunk development resources and receive a 10GB license to build an app that will help solve use cases for customers all over the world. Splunkbase has 1000+ apps from Splunk, our partners and our community. Find an app for most any data source and user need, or simply create your own with help from our developer portal.