







The Anomali Community App for Splunk provides the following functionality:
Download and view Weekly Threat Briefings and Breaking News reports, published by Anomali Labs.
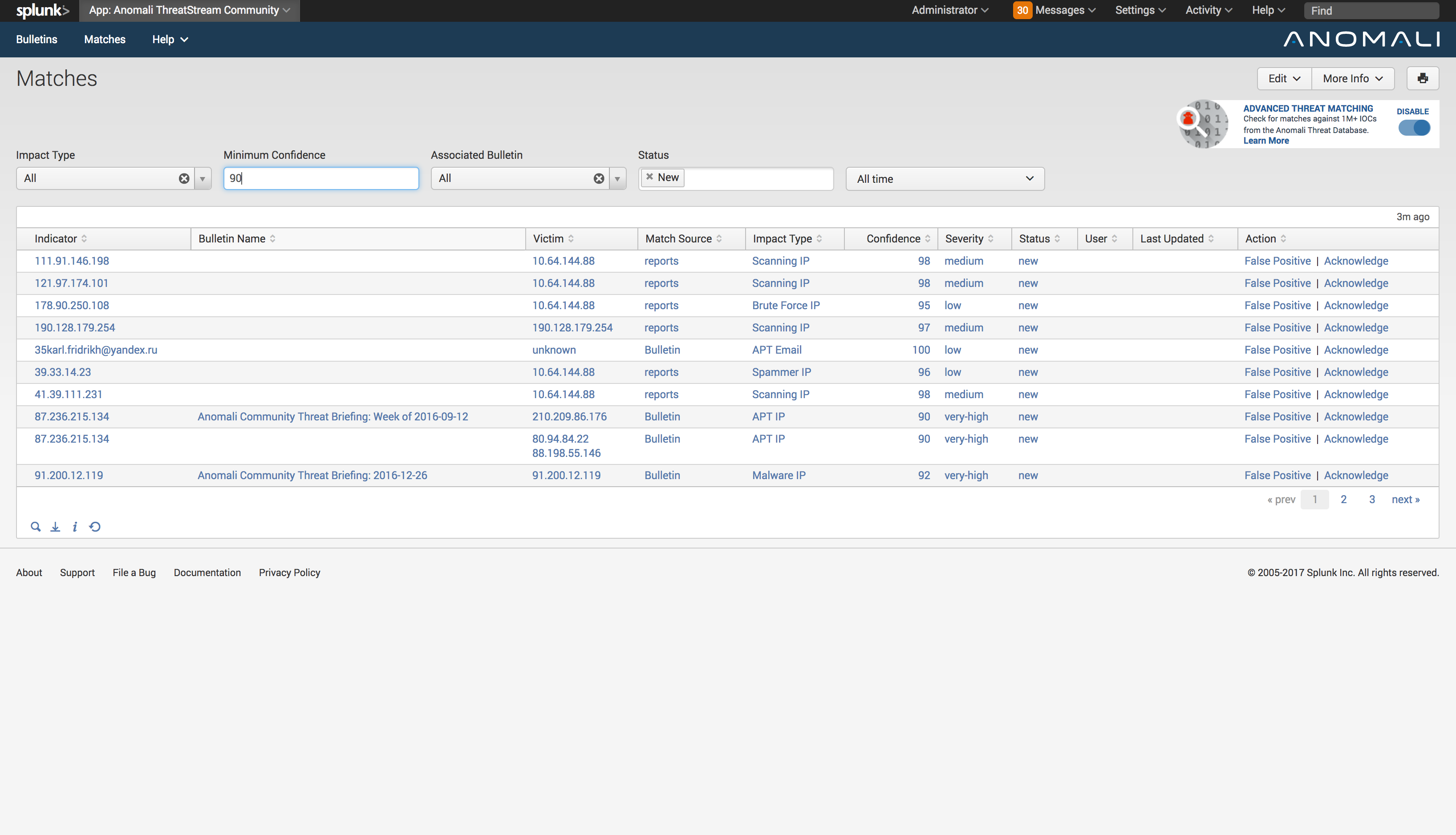
Scan logs against Anomali content to identify threats in your environment.
Optionally upload log summaries to cloud scanning against millions of Indicators of Compromise.
Investigate and Respond to threats identified within your environment.
Overview:
https://www.anomali.com/files/eng/SplunkCommunityApp.mp4
Installation:
https://www.anomali.com/files/eng/CommunityAppSetup.mp4
Quick Start Guide:
https://www.anomali.com/files/eng/Anomali-Community-App-for-Splunk-Quick-Start-Guide.pdf
System Requirements:
Feedback:
We value your feedback and will continue to update this app on a regular basis. Please send comments, requests, or feedback to splunk@threatstream.com.
Addressed feedback from Splunk certification team
Bug Fixes
Updated the product logos
Fixes for the Default Dashboard
Added new Dashboards
UI improvements.
Fixes an issue with indexers receiving unnecessary files.
Note, Current ThreatStream customers will need to install the latest version of Optic Link (4.9.8). Please see the Optic.threatstream.com in the Docs section to download this splunk version.
As a Splunkbase app developer, you will have access to all Splunk development resources and receive a 10GB license to build an app that will help solve use cases for customers all over the world. Splunkbase has 1000+ apps from Splunk, our partners and our community. Find an app for most any data source and user need, or simply create your own with help from our developer portal.